MAC (Media Access Control) addresses are unique identifiers assigned to network interface controllers (NICs) of devices connected to a network. Every device connected to a network, including computers, smartphones, printers, routers, and switches, has a unique MAC address. These addresses are used by network protocols to identify and communicate with each device on the network.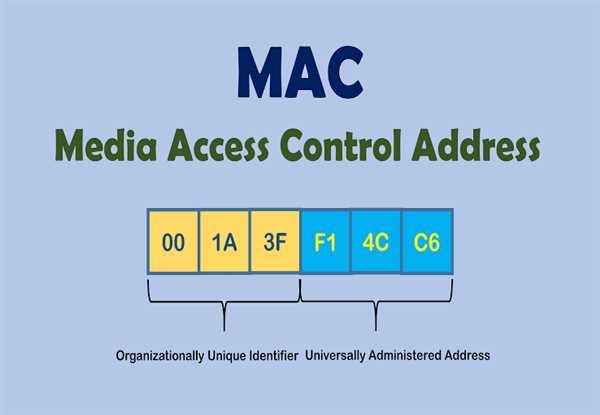
A MAC address is a 48-bit (6-byte) number that is typically represented as a sequence of 12 hexadecimal digits. The first half of the address (the first 24 bits) is assigned by the manufacturer of the device and is known as the Organizationally Unique Identifier (OUI). The second half of the address (the last 24 bits) is assigned by the manufacturer and is used to identify the specific device.
MAC addresses are used by network protocols such as Ethernet to control the flow of data between devices on a network. When a device wants to send data to another device, it first needs to obtain the MAC address of the destination device. This is done using the Address Resolution Protocol (ARP), which allows a device to map an IP address to a MAC address.
When a device receives data from another device, it checks the destination MAC address to determine whether the data is intended for it. If the MAC address matches the address of the receiving device, the data is processed. If the MAC address does not match, the data is discarded.
MAC addresses are also used by network switches to forward data to the appropriate destination. When a switch receives data from a device, it checks the destination MAC address to determine which port the data should be forwarded to. This allows switches to selectively forward data to specific devices on the network, improving network performance and security.
While MAC addresses are unique and can be used to identify individual devices on a network, they can also be changed or spoofed. This can be done for various reasons, such as to bypass network restrictions or to hide the identity of a device. However, changing or spoofing a MAC address can also be used for malicious purposes, such as impersonating another device on the network or conducting a man-in-the-middle attack.